Everything for link and flow security
In addition to its range of access links, Sewan offers a wide range of value-added services to ensure the security of links, Internet connections and the data transmitted over them.
A complete solution
Security at every level of the network
Sewan's core network infrastructures are natively redundant and backed up to guarantee maximum availability of all our services with a multi-operator, multi-technology architecture.

A secure backbone
The heart of the Sewan network is spread across several datacentres. Each piece of equipment is redundant on 2 different sites and has automatic failover or load-sharing mechanisms.
Infrastructure and VPN/MPLS
A VPN/MPLS solution for building your own private, watertight IP MPLS network with secure, high-performance and highly available Internet access.
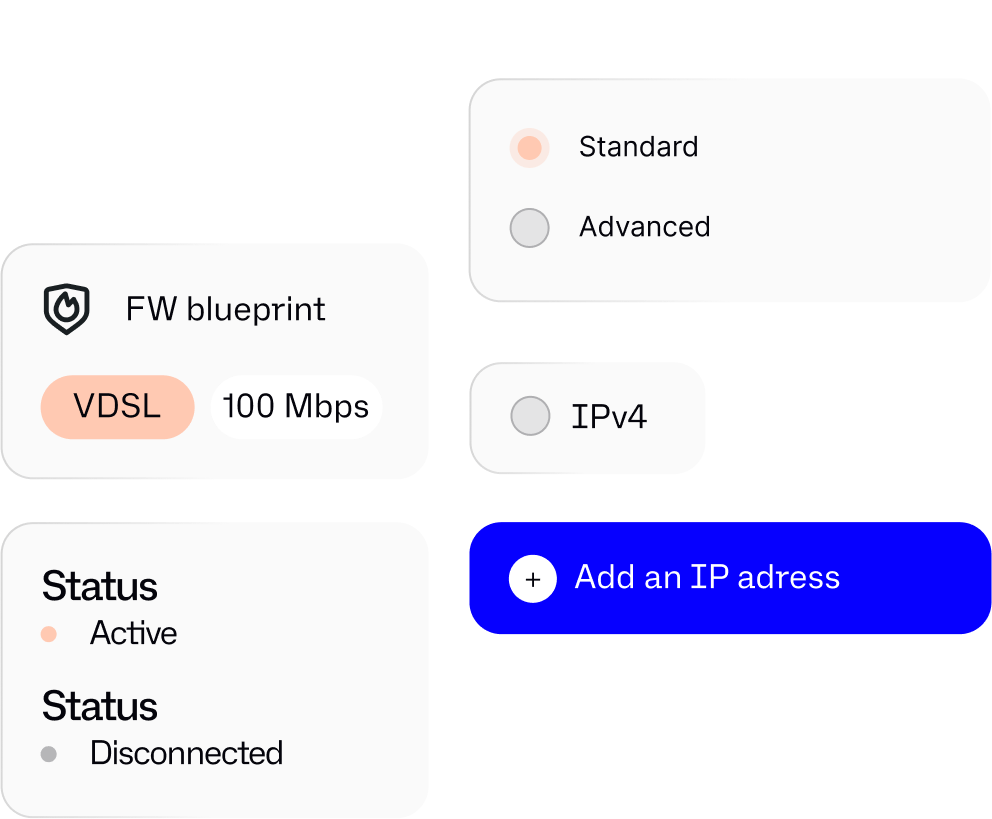
Cloud Firewall
A 100% automated Cloud Firewall that enables centralised management of your own confidentiality policy to ensure the highest possible level of security.


Sophia, the Co-pilot for Partners